AI-powered threat
detection platform
#AI4REAL
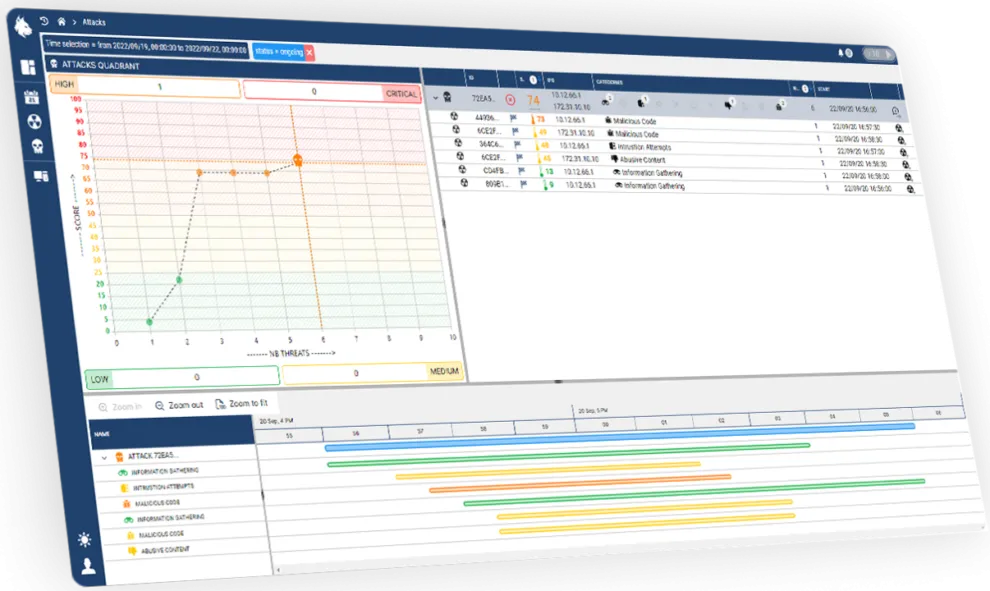
NDR Custocy enables you to detect what other tools can't see by providing complete monitoring of your computer network.
Free demoCustocy is a unique collaborative AI technology that identifies sophisticated and unknown (zero-day) attacks. Born from our research laboratory, our AI models ensure effective protection for your computer network with unprecedented detection accuracy and speed.
Equip your organization with an advanced defense tool and increase the productivity of your security teams.
The Custocy cyber platform combines artificial intelligence, behavioural analysis and threat intelligence ensuring 88 times less false positives.
Detection of Zero-Day attacks
Our anomaly detection technique using AI and our multiple sources of Threat Intelligence allow us to detect anomalous behaviour and zero-day threats.
Advanced Persistent Threat Detection
Using a multi-temporal view, our AI models detects and correlates new and sophisticated threats that persist over time.
Improved efficiency
Empower analysts with a powerful real-time threat detection tool to save time and increase productivity and responsiveness of the SOC. The Custocy interface automatically correlates events, freeing analysts from being overwhelmed by an avalanche of alerts.
Adapts to you environment
The Custocy NDR platform is autonomous and can integrate with your existing ecosystem (SIEM, XDR, EDR, etc.). Our advanced AI models learn and adapt to your network architecture, regardless of its size and composition. Deployment is quick and efficient.

Unparalleled detection of attacks thanks to our core technology: the METALEARNER
The Metalearner is a unique collaborative AI technology developed within our research laboratory. It was created using a multi-temporal approach to detect complex and unknown (zero-day) attacks with high accuracy and 88 times less false positives.
How does the Metalearner work?
It orchestrates multiple AIs, each operating at different time scales, from short to long, to detect various types of threats. It then makes the decision to alert the analyst or not, indicating a severity score.
It could be you
204
is the average time from initial access to impact
Source: IBM Data Breach Report 2023
75
of victims had an up-to-date EDR solution
Source: purplesec.us
72
use lateral movement
Source: vmware.com
5
It's the average time it takes cybercriminals to break into a company's environment.
Source: SANS Hacker Survey 2022
Latest news

The TCP Reset, the Magical Solution of NDR for Automatic Response?

Custocy accelerates growth with its sovereign NDR solution

Native XDR VS Hybrid XDR: How to choose?

How a NDR Solution Detects Attacks on an Encrypted Network?

